AgixCyber Expertise
- OT CYBERSECURITY ARM FOR MSEs, MSPs
- OT IDS SOLUTIONS
- OT ASSET INVENTORY
- VULNERAVILITY MANAGEMENT
- EOL DEVICES SECURITY CONTROLS
- OT NETWORK DESIGN AND MANAGEMENT
- BACKUP AND RESTORATION
- OT RISK ASSESSMENT AND MANAGEMENT

OT Cybersecurity Arm for MSEs, MSPs
An OT Cybersecurity Arm is a dedicated unit, service line, or division within a company or MSP that specializes in securing Operational Technology (OT) — the hardware and software systems used to control physical devices, processes, and infrastructure. Focusing on protecting industrial systems like SCADA, PLCs DCS, etc which are widely used in Manufacturing, Oil & Gas, Energy/utilities, Transportation etc.
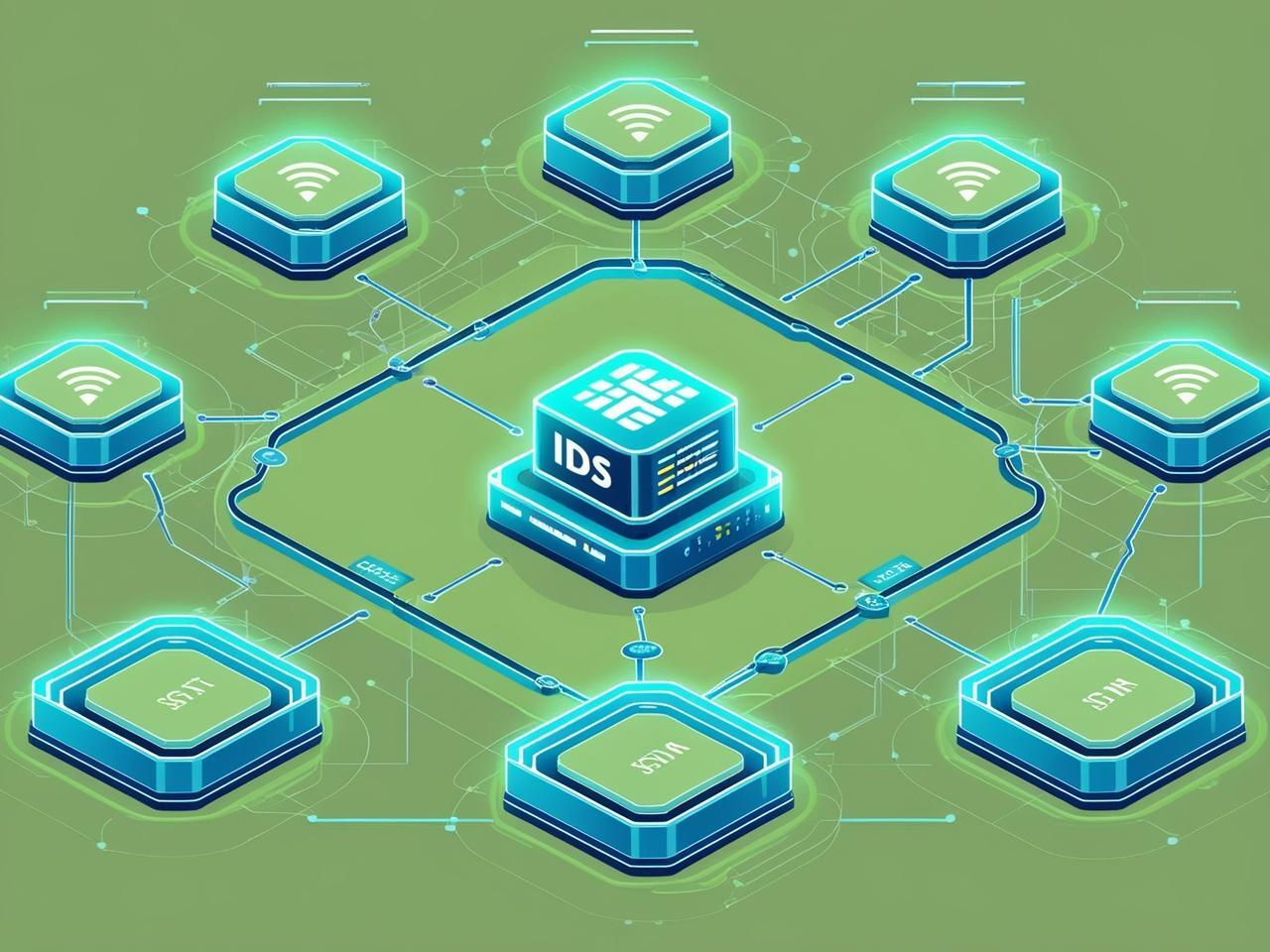
OT IDS Solutions
Intrusion Detection System is a cybersecurity solution designed to monitor and detect malicious or abnormal activity within Operational Technology (OT) networks — such as those running factories, power plants, or transportation systems.
It works by analyzing traffic and behavior in industrial control systems (ICS) and alerting on threats, policy violations, or unusual behavior that could indicate a cyberattack, equipment failure, or insider misuse.
OT Asset Inventory
Vulnerability Management
EOL Devices Security Controls
EOL (End-of-Life) devices are systems, hardware, or software that the vendor no longer supports or updates — meaning:
- No more security patches
- No technical support
- No compatibility assurance with newer systems
In OT (Operational Technology) environments, EOL devices are very common, including old PLCs, HMIs, Windows XP/7 systems, and legacy SCADA servers — because replacing them is expensive, disruptive, or technically difficult.
OT Network Design and Management

Backup and Restoration
In OT cybersecurity, backup and restoration refers to the regular process of saving and recovering critical configurations, data, and logic from industrial systems (e.g., PLCs, HMIs, SCADA servers) to ensure operational continuity after a cyberattack, failure, or accidental change.
Partners












Contact Us

